As first reported by Cyber Security News, 2024 and 2025 have seen a dramatic rise in cyberattacks against global healthcare systems, driven by advanced persistent threat (APT) groups tied to Iran, North Korea, and China.
These attackers exploit both IT and operational technology (OT) environments, deploying malware and ransomware designed not only to steal sensitive research data but to actively disrupt diagnostic equipment, laboratory systems, and even life-support devices. The May 2025 ICS-CERT advisory warned specifically about a severe memory corruption flaw in Pixmeo OsiriX MD software that could allow credential theft or system crashes in clinical environments.
DICOM Protocols Exploited to Tamper with Imaging and Patient Data
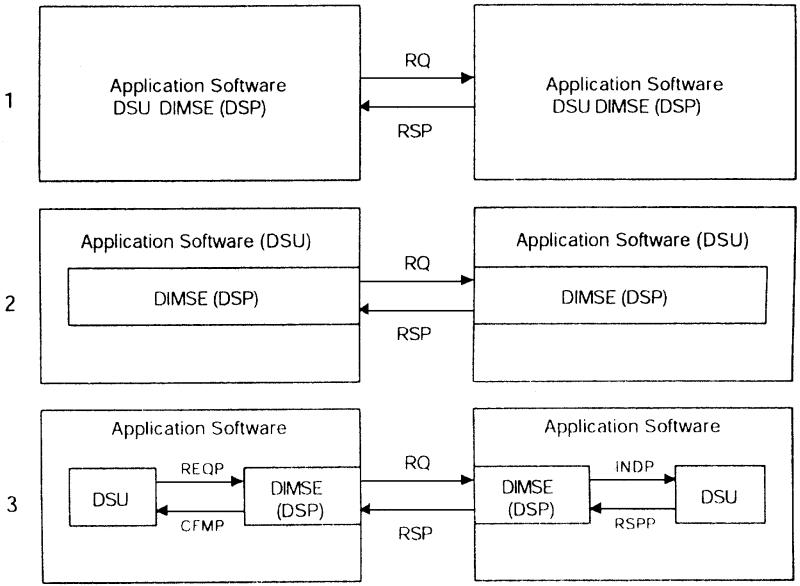
A key vector of these attacks involves the manipulation of DICOM (Digital Imaging and Communications in Medicine) protocols.
Source: nih.gov.
Analysts have uncovered a rise in malware-infected DICOM viewer software posing as legitimate tools from brands like Philips and Siemens, enabling attackers to deploy remote access tools and gain control of medical imaging devices. In some cases, the malware could even manipulate scans to inject fake tumors, raising serious concerns about diagnostic sabotage.
Combined with major ransomware incidents like ALPHV’s attack on Change Healthcare and Qilin’s breach of Synnovis, these evolving threats highlight the urgent need for stronger defenses—such as IT-OT segmentation, multi-factor authentication, and continuous monitoring—to protect both patient data and lives.