The FBI has issued a warning that hackers tied to Russia’s Federal Security Service (FSB) are actively targeting critical infrastructure organizations by exploiting a long-known Cisco vulnerability. The threat group, tracked as Berserk Bear (also known as Blue Kraken, Crouching Yeti, Dragonfly, and Koala Team), has been using the seven-year-old flaw CVE-2018-0171 to infiltrate networks. The bug, found in Cisco’s Smart Install feature for IOS and IOS XE software, enables attackers to remotely reload unpatched devices—causing denial-of-service disruptions—or even execute arbitrary code.
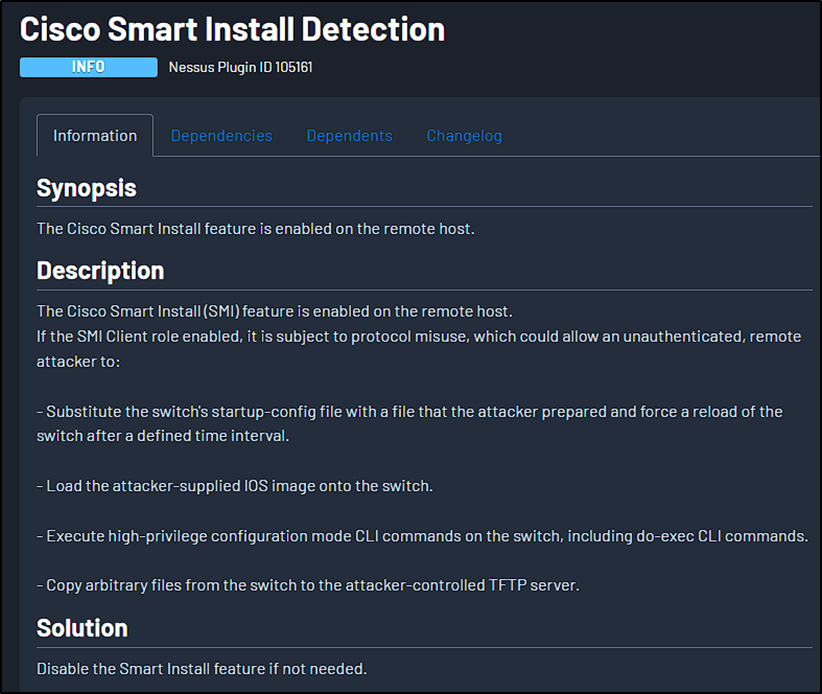
Source: cisco.com.
According to the FBI, in the past year these state-backed actors have gathered configuration files for thousands of U.S. networking devices across critical infrastructure sectors. In some cases, they modified the files to maintain unauthorized access, conducting reconnaissance on protocols and applications tied to industrial control systems (ICS). This interest signals a potential for more disruptive operations targeting essential services.
This is not the first time Berserk Bear has engaged in such campaigns. The group has a long history of targeting U.S. state and local governments, aviation networks, and SLTT entities. Cisco has also confirmed increased exploitation of CVE-2018-0171, with its Talos division observing aggressive activity from related Russian threat actors, such as Static Tundra, against telecom, manufacturing, and higher education organizations worldwide.
Attackers are also leveraging advanced tools to entrench themselves within victim networks. These include custom SNMP utilities for persistence and the notorious SYNful Knock firmware implant, a backdoor first discovered in 2015. Cisco warns that while Russia is leading this wave of exploitation, other state-backed groups are likely using the same weakness, making unpatched devices especially high-risk.
Healthcare organizations rely heavily on connected medical devices, secure communications, and reliable infrastructure—making them prime targets for nation-state groups exploiting old vulnerabilities. Hospitals, clinics, and research institutions should ensure all Cisco networking equipment is fully patched and that Smart Install is disabled if not required. Network segmentation, strict monitoring of device configurations, and proactive detection of abnormal traffic patterns are essential safeguards. In a sector where downtime can directly impact patient safety, maintaining strong patch management and ICS protection must remain a top security priority.







