The Pakistan-linked APT36 cyber-espionage group has been observed abusing Linux .desktop files in a renewed campaign targeting Indian government and defense entities. The operation, first detected on August 1, 2025, is ongoing and aims to achieve data exfiltration and long-term surveillance, according to threat intelligence reports from CYFIRMA and CloudSEK.
The attackers deliver malicious .desktop files via phishing emails inside ZIP archives, camouflaging them with PDF-like names. When opened, these files execute a hidden bash command through the Exec= field. This command downloads and launches a hex-encoded payload, while simultaneously displaying a benign PDF in Firefox to avoid raising user suspicion. The technique effectively turns .desktop launchers—normally simple configuration shortcuts—into stealthy malware droppers.
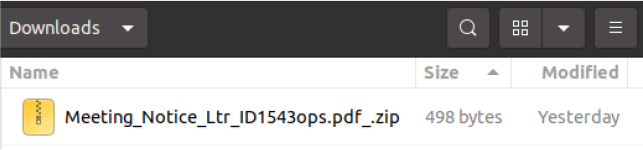
A malicious payload with the malware. Source: cyfirma.com.
To evade detection, APT36 employs several tricks: disabling terminal visibility (Terminal=false), enabling autostart (X-GNOME-Autostart-enabled=true), and dropping Go-based ELF executables that can persist via cron jobs or systemd services. These payloads open a WebSocket communication channel to attacker-controlled servers, enabling remote command execution and continuous data theft.
Because .desktop file abuse remains underreported in Linux security tooling, these attack vectors often fly under the radar. The group’s use of both Google Drive and attacker-owned infrastructure for payload delivery and decoy display further enhances the campaign’s legitimacy and stealth.
While this campaign currently targets government and defense sectors, the abuse of .desktop files as malware launchers signals a broader threat to any Linux-based environment—including healthcare networks increasingly relying on Linux servers and devices. Security teams should immediately implement detection rules for abnormal .desktop file behavior, scan for hidden executable payloads in /tmp/, and educate staff to avoid opening suspicious files—even if they appear to be PDFs. Strengthening endpoint monitoring, particularly for Linux systems, is crucial in preventing stealthy malware like APT36’s from establishing persistent access to sensitive patient data or operational systems.