Security researcher Sud0Ru has unveiled a new method to stealthily harvest credentials from Windows systems that bypasses most Endpoint Detection and Response (EDR) tools. The technique exploits legitimate but under-monitored Windows API functions, allowing attackers with local admin privileges—not even SYSTEM-level access—to extract secrets from sensitive registry hives like SAM and SECURITY without tripping common security alerts.
The approach hinges on two obscure Windows internals. First, attackers use the undocumented NtOpenKeyEx function with the REG_OPTION_BACKUP_RESTORE flag, enabling access to protected registry keys while sidestepping Discretionary Access Control Lists (DACLs). This is possible through the SeBackupPrivilege, which is available to local administrators by default. Next, instead of using heavily monitored functions like RegQueryValueExW, the method employs RegQueryMultipleValuesW to discreetly read encrypted values from the registry.
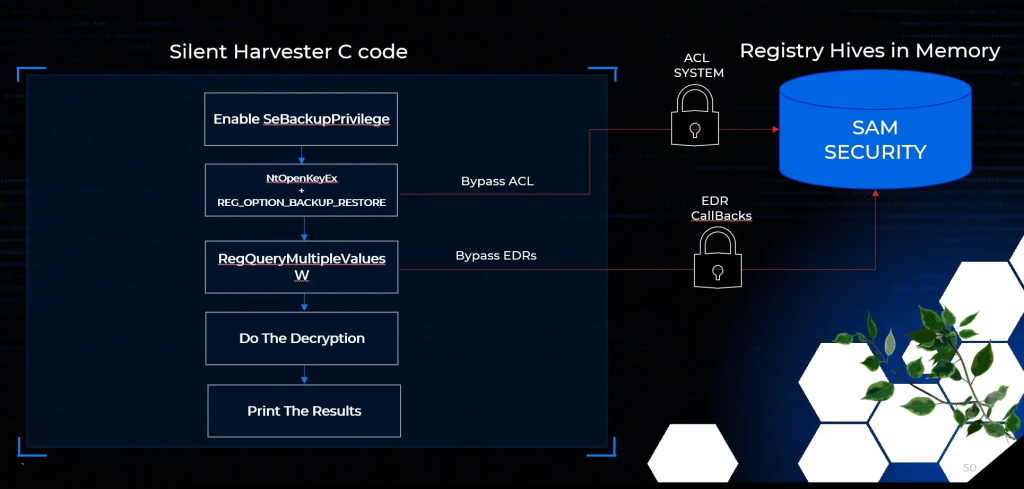
Stealthy data exfiltration. Source: Cyber Security News / Sud0Ru.
By leveraging these lesser-known APIs, attackers can avoid detection by EDR products that rely on kernel-mode callbacks to monitor specific registry access and common API calls. Because the entire process runs in memory and avoids creating disk artifacts, it leaves almost no forensic trace.
What makes this method particularly dangerous is its ability to operate within the gray zones of the Windows security model. It doesn’t exploit vulnerabilities, nor does it rely on malware or process injection. Instead, it abuses legitimate, underused functionality in Windows to achieve its goal. While the secrets themselves still need to be decrypted in a separate step—requiring additional data from the SYSTEM hive—the exfiltration technique alone demonstrates a powerful bypass of otherwise mature detection systems.
This silent credential theft technique poses a serious threat to healthcare organizations where Windows systems manage sensitive clinical, operational, and identity data. Security teams must rethink the assumption that administrative privilege equates to limited exposure. Consider enhancing EDR visibility around backup and registry-related APIs, auditing SeBackupPrivilege usage, and hardening systems against in-memory attacks. In environments that handle protected health information (PHI), undetected lateral movement enabled by stolen credentials can result in widespread compromise—making proactive detection of these obscure techniques an urgent priority.