Cybersecurity researchers have identified a deceptive Go module named golang-random-ip-ssh-bruteforce that masquerades as a hacking utility while surreptitiously stealing sensitive information. Published on pkg.go[.]dev in June 2022 and tied to a GitHub account called IllDieAnyway (G3TT), the tool scans random IPv4 addresses for exposed SSH services, attempts brute-force logins with weak credentials, and forwards successful login details to a Telegram bot operated by the attacker.
The malware disables host key verification, allowing it to connect indiscriminately to any SSH server without checking its authenticity. Once it achieves a successful login, it immediately exfiltrates the target IP, username, and password to the Telegram bot @sshZXC_bot, which is linked to an account named @io_ping. This stealthy design ensures that operators unknowingly funnel useful credentials to the threat actor, while Telegram’s HTTPS-based communication makes the traffic appear like normal web requests.
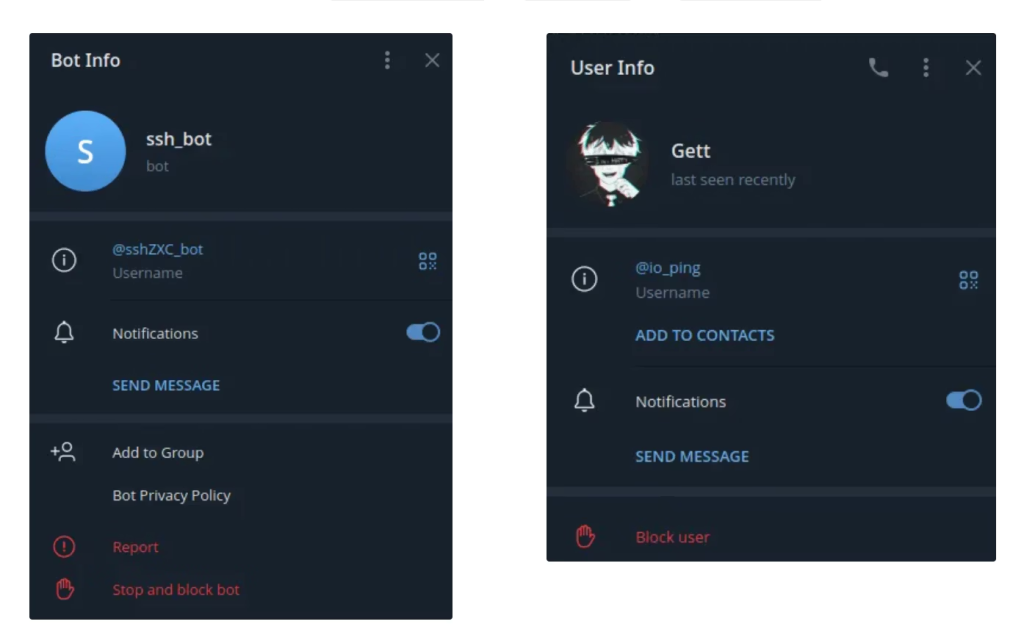
Source: socket.dev.
Beyond this module, archived evidence shows that the developer also created other hacking tools, including port scanners, an Instagram parser, and a PHP-based botnet called Selica-C2. Their YouTube presence, featuring tutorials on hacking Telegram bots and launching SMS spam campaigns, suggests a strong background in cybercrime, with researchers assessing the individual as likely Russian.
Researchers warn that the package not only spreads risk across unwitting users’ IPs but also maximizes efficiency by immediately halting after one valid login is captured. By leveraging the Telegram Bot API, the attacker ensures that stolen data blends into ordinary outbound traffic, slipping past many network defenses and making detection difficult.
For healthcare and medical organizations, this discovery highlights the hidden risks of supply chain malware in open-source ecosystems. Security teams should implement strict code provenance checks before introducing external modules into production environments, continuously monitor egress traffic for unusual but seemingly legitimate HTTPS requests, and enforce least-privilege access for SSH accounts. Given healthcare’s reliance on secure remote access for critical systems, organizations must pair strong credential hygiene with monitoring tools that can detect subtle exfiltration patterns masked as normal traffic.



