Cybersecurity researchers at Fortinet have discovered a phishing campaign that uses fake voicemails and purchase order notifications to deliver a malware loader dubbed UpCrypter. Beginning in August 2025, the campaign has primarily affected industries such as healthcare, manufacturing, construction, technology, and retail across countries including Austria, India, Pakistan, Canada, Egypt, and Belarus.
Attackers craft phishing emails that link to visually convincing landing pages, which mimic corporate branding by using the victim’s domain and logo. These pages prompt users to download ZIP files disguised as voicemail recordings or PDF documents. Inside lies a JavaScript file that initiates a multi-stage malware deployment process once executed.
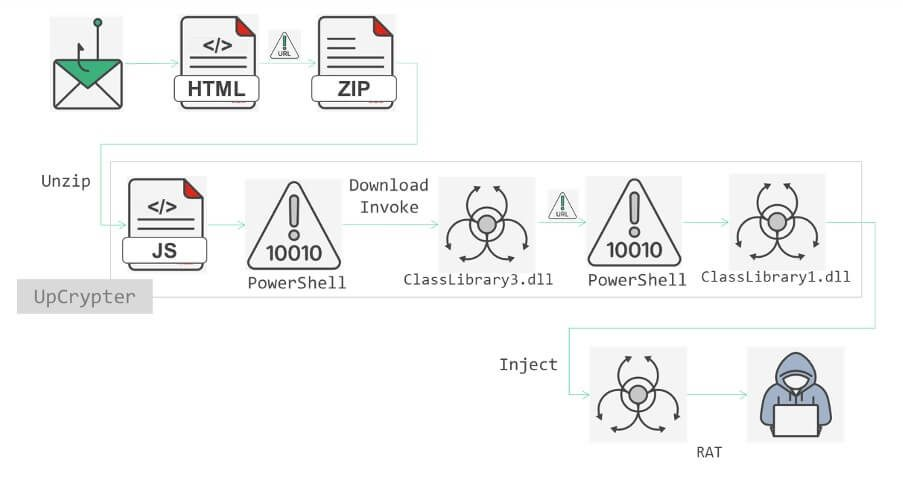
Attack flow. Source: fortinet.com.
Stealthy, layered malware deployment
The downloaded JavaScript file contacts a command-and-control server to fetch UpCrypter—but only after scanning for security tools and ensuring the system isn’t being analyzed in a sandbox. UpCrypter then downloads additional payloads: typically a PowerShell script, a DLL, and the main RAT payload, using obfuscation and anti-forensics techniques like in-memory execution and steganography.
The final payload is one of several remote access trojans—PureHVNC, DarkCrystal RAT (DCRat), or Babylon RAT—each capable of giving attackers full remote control over the infected host. The malware avoids traditional file writes, making detection and forensic tracing extremely difficult.
LOTS tactics and evasion using trusted platforms
The UpCrypter campaign isn’t happening in isolation. It coincides with a broader rise in “living-off-trusted-sites” (LOTS) tactics, where threat actors exploit legitimate services like Google Classroom, OneNote, SendGrid, and Zoom to host malicious content or distribute phishing lures. For instance, another large-scale attack abused Google Classroom to send over 115,000 phishing emails in under a week, bypassing standard email defenses such as SPF, DKIM, and DMARC.
Threat actors have also adopted advanced client-side evasion techniques such as JavaScript-based anti-analysis scripts, Browser-in-the-Browser (BitB) deception, and virtual desktop hosting via noVNC. These methods help phishing pages dodge both human scrutiny and automated scanning, reinforcing the trend toward more evasive and persistent social engineering tactics.
Advice for healthcare security professionals
For healthcare and medical security professionals, the UpCrypter campaign underscores the growing threat posed by highly targeted phishing attacks that bypass traditional defenses. These campaigns exploit user trust, mimic internal communications, and use evasive malware loaders to deliver remote access trojans that can compromise patient data, disrupt care delivery, and enable long-term surveillance.
To counter these threats, healthcare organizations should:
- Harden email defenses with advanced phishing detection tools that go beyond SPF/DKIM/DMARC.
- Train staff regularly to recognize and report phishing attempts, especially those posing as voicemails or order confirmations.
- Implement endpoint monitoring for in-memory execution and unusual PowerShell activity.
- Restrict internet access from clinical systems not needing external communication.
- Isolate high-risk applications and enforce strict least-privilege policies.
Proactive, layered defenses and continuous awareness training remain essential as phishing tactics evolve.







