A newly identified zero-day, CVE-2025-53690, has been exploited in the wild, with serious implications for healthcare organizations that still depend on legacy Sitecore platforms for patient portals, scheduling systems, or online services. The flaw arises from a sample ASP.NET machine key included in Sitecore’s pre-2017 documentation. Some administrators mistakenly deployed this key in production systems, leaving healthcare websites and portals vulnerable to remote code execution (RCE) attacks.
Threat actors are abusing the /sitecore/blocked.aspx endpoint, where an unauthenticated ViewState field can be manipulated using the reused machine key. Once triggered, attackers achieve code execution under the IIS NETWORK SERVICE account, enabling them to install a reconnaissance backdoor called WeepSteel. For healthcare environments, this presents an especially dangerous risk: the malware can silently collect host, network, and process data, disguising its activity as legitimate traffic.
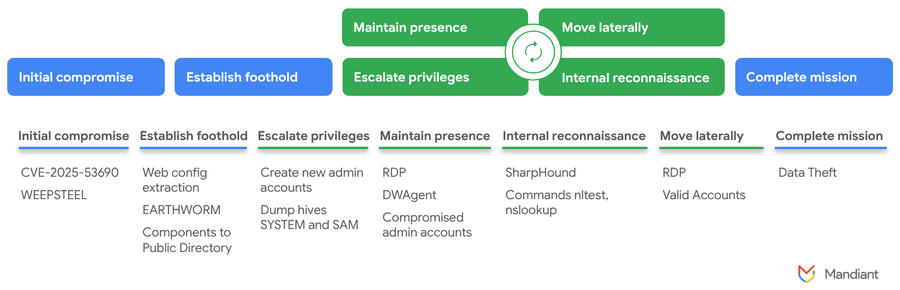
The attack lifecycle. Source: cloud.google.com.
Mandiant’s investigation shows that after deploying WeepSteel, attackers execute a series of reconnaissance commands and then escalate operations by installing tools such as Earthworm (network tunneling), Dwagent (remote access), and 7-Zip (for archiving stolen files). They also create local administrator accounts (asp$, sawadmin), dump cached credentials, and attempt token impersonation. In a healthcare context, this could open access pathways to sensitive electronic health records (EHRs), billing systems, or imaging data repositories.
Persistence techniques include disabling password expiration, enabling RDP access, and registering Dwagent as a SYSTEM service. These measures make it easier for attackers to maintain long-term access — a dangerous scenario in healthcare, where systems often run continuously and downtime directly impacts patient care.
The vulnerability affects Sitecore Experience Manager (XM), Experience Platform (XP), Experience Commerce (XC), and Managed Cloud up to version 9.0, but only if deployed with the vulnerable sample key. Products like XM Cloud, Content Hub, and OrderCloud are not impacted. However, many healthcare organizations that adopted Sitecore for web-facing services prior to 2017 may still be at risk if machine keys were never updated.
Sitecore, working with Mandiant, has issued a security bulletin urging all organizations — including hospitals and health systems — to replace static <machineKey> values in web.config immediately with unique, randomly generated keys and encrypt the <machineKey> element. Ongoing rotation of static keys is strongly recommended to prevent future exploitation.
Healthcare organizations relying on legacy Sitecore deployments should treat CVE-2025-53690 as an urgent priority. Outdated machine keys create hidden entry points that sophisticated attackers can use to infiltrate systems, establish persistence, and potentially move laterally toward protected health information (PHI). IT leaders should audit all Sitecore-based portals, replace and encrypt machine keys, rotate keys regularly, and review environments for signs of intrusion. Protecting patient trust and safeguarding care delivery requires treating web platform security as part of the broader clinical safety mandate.







