ESET researchers have disclosed a sophisticated new cyber threat cluster named GhostRedirector, which has already compromised at least 65 Windows servers worldwide, including in sectors like healthcare, education, insurance, and retail. The campaign uses two key tools: a C++ backdoor called Rungan and a malicious IIS module named Gamshen, both working together to establish persistence and conduct search engine manipulation.
Gamshen is designed to deceive Google’s search crawlers, injecting backlinks to artificially promote external gambling sites. Though this doesn’t impact regular web users directly, participation in such SEO fraud can severely damage a healthcare organization’s online trust and credibility. Compromised web servers may unwittingly promote unethical or illegal content while hosting patient-facing portals.
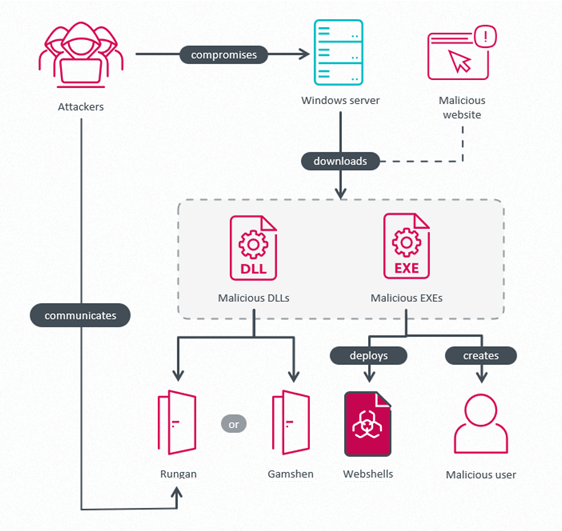
Attack overview. Source: welivesecurity.com.
Initial access is believed to come through SQL injection flaws, after which the threat actor uses PowerShell via SQL Server to install payloads. Once active, Rungan allows remote command execution, account creation, and more. Supporting tools include remote desktop backdoors like GoToHTTP and privilege escalation utilities like BadPotato—highlighting the group’s interest in maintaining persistent, stealthy access.
Healthcare systems are especially at risk due to common reliance on legacy IIS servers and web applications that may lack regular patching. The attackers also deploy reconnaissance tools like Zunput to map out hosted web content and drop backdoors, creating opportunities for data exfiltration or lateral movement within networks.
Attribution indicators suggest China-based operations, consistent with previous campaigns like those linked to DragonRank, which used similar IIS-based malware for SEO fraud. The GhostRedirector group appears well-resourced and deliberate in maintaining long-term control over compromised environments.
Healthcare organizations must treat this campaign as a critical warning to audit their public-facing servers, especially those running IIS. SEO abuse may seem minor compared to ransomware, but it’s often a foot in the door to deeper compromise. Prioritize patching, web app security reviews, and IIS module integrity checks—before passive SEO abuse evolves into patient data breaches or ransomware deployment.







