Russian state-aligned threat actor APT28 has been linked to a novel Outlook-based malware called NotDoor, used in attacks across NATO-aligned nations—including sectors critical to national infrastructure like healthcare. NotDoor is engineered as a Visual Basic for Applications (VBA) macro embedded in Microsoft Outlook, where it activates silently upon receiving specific email triggers. Once activated, it gives attackers the ability to steal data, drop malicious files, and run system commands using Outlook’s built-in event functionality.
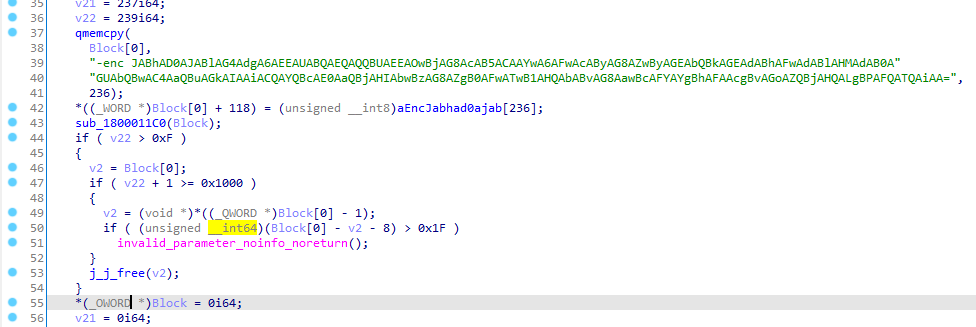
Encoded PowerShell command. Source: lab52.io.
The infection process utilizes DLL side-loading via Microsoft’s OneDrive binary to deliver a malicious DLL that disables macro warnings and deploys the backdoor. Once installed, NotDoor executes obfuscated PowerShell commands that contact a remote command-and-control server, alter the Windows Registry for persistence, and suppress Outlook dialogs that might alert users.
Notably, the malware creates and uses a %TEMP%\Temp folder to stage stolen data, which it sends to a Proton Mail address before self-deleting to reduce detection. The attack is triggered by emails with phrases like “Daily Report,” allowing the malware to run hidden commands or send/receive files as email attachments.
The healthcare sector is especially vulnerable, as Outlook is commonly used for scheduling, care coordination, and sensitive communications. The malware’s ability to operate through routine tools increases the risk of undetected lateral movement and long-term data leakage. Its four supported commands—ranging from silent execution (cmdno) to file exfiltration (dwn)—make it suitable for long-term espionage and data harvesting.
In parallel, Chinese group Gamaredon (APT-C-53) has been seen using Telegram’s Telegraph and Microsoft Dev Tunnels to obfuscate command infrastructure. Their tools rely on frequently rotating domains and cloud abuse to make their operations nearly untraceable. The campaign also involves USB-propagating malware distributed via spoofed Cloudflare Workers domains, introducing added risk for hospitals where removable media are still in use.
For medical and healthcare IT leaders, NotDoor highlights the urgent need to monitor and lock down email macros and closely control cloud-exposed endpoints like Outlook. Implement strict macro policies, deploy behavioral threat detection tools, and reinforce email gateway protections. In environments where Outlook is essential, healthcare security teams must treat it as a potential attack surface—not just a communication tool—and scrutinize even the most trusted apps for signs of compromise.