Six of the most popular password managers—including 1Password, Bitwarden, Enpass, iCloud Passwords, LastPass, and LogMeOnce—are vulnerable to unpatched clickjacking attacks that could let hackers steal credentials, 2FA codes, and payment data. The flaws affect browser-based versions and were revealed at DEF CON 33 by security researcher Marek Tóth, with confirmation from cybersecurity firm Socket.
Source: wikipedia.org.
Despite the severity of the issue, the vulnerabilities remain unaddressed across tens of millions of user accounts.
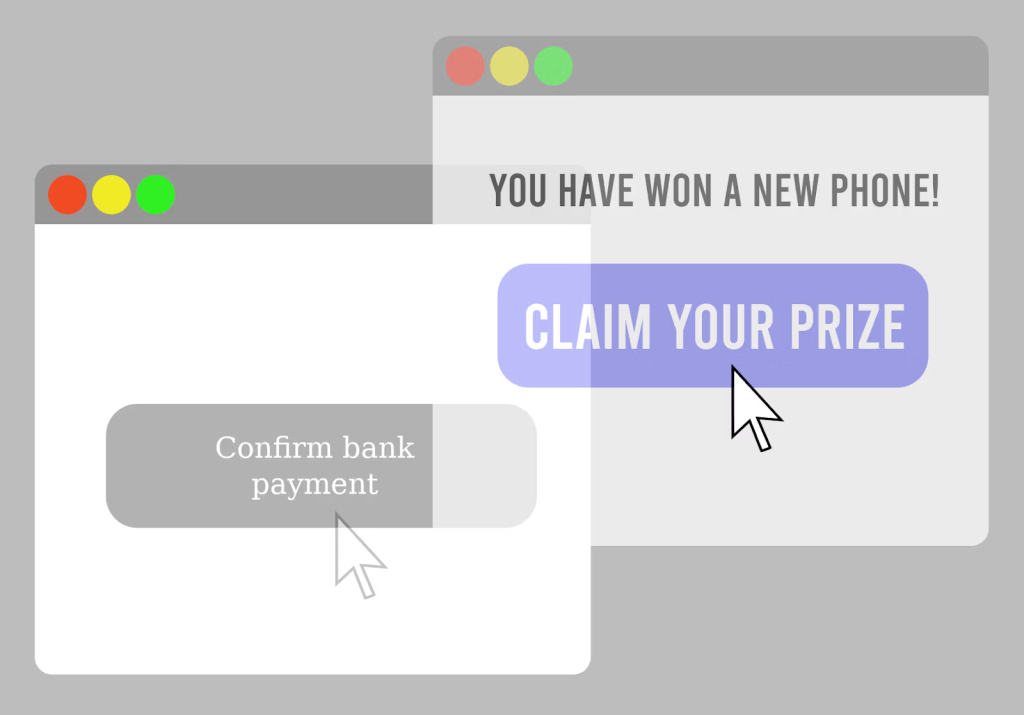
The attacks work by embedding invisible HTML overlays onto malicious or compromised websites. These overlays trick users into clicking on hidden elements in the password manager interface, triggering autofill actions and leaking sensitive data without the user realizing it. The attack can be disguised as everyday elements like cookie banners or CAPTCHA popups, and some variants even cause the autofill UI to follow the user’s cursor to ensure any click activates it.
Tóth tested 11 major password managers and found all were vulnerable to at least one attack method. He also demonstrated a universal script that can detect which password manager is active and adapt the attack in real time. Until vendors issue patches, users are advised to disable autofill features in browsers and remain vigilant when interacting with overlays or popups on unfamiliar websites.
Given the high sensitivity of patient and clinical data, healthcare and medical professionals should immediately disable browser-based autofill in password managers and avoid entering credentials on unfamiliar or unsecured websites to prevent credential leakage and HIPAA violations.