A new macOS-targeting infostealer dubbed Shamos has emerged, deployed through ClickFix attacks that masquerade as legitimate troubleshooting advice. Identified by CrowdStrike, Shamos is a variant of the Atomic macOS Stealer (AMOS) and was developed by the cybercriminal group known as COOKIE SPIDER. The malware is capable of stealing credentials, keychain items, Apple Notes, browser data, and cryptocurrency wallets. Since June 2025, Shamos has been observed targeting over 300 environments globally.
Shamos is distributed through malicious ads and spoofed GitHub repositories that pose as solutions to common macOS issues—like printer errors or software glitches. These ClickFix campaigns trick users into copying Terminal commands under the guise of system fixes. Instead, these commands decode a Base64 string that downloads a malicious Bash script, which captures the user’s password, bypasses Gatekeeper protections, and launches the malware.
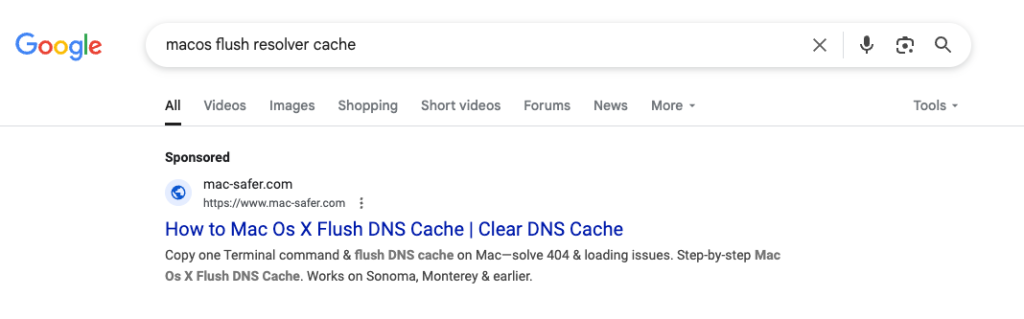
Search engine results promoting the malvertising website. Source: crowdstrike.com.
Once installed, Shamos performs system reconnaissance, extracts sensitive data, and exfiltrates it to the attacker in a compressed archive via curl. If granted sudo privileges, the malware ensures persistence by installing a LaunchDaemon and can drop additional payloads like a fake Ledger Live app or botnet module. The use of AppleScript and anti-VM checks allows it to stealthily operate and evade detection in virtualized environments.
This method of social engineering is particularly insidious because it leverages the trust users place in online technical advice. ClickFix-style malware deployment is now a favored tactic not just among cybercriminals, but also nation-state actors and ransomware operators. The success of these campaigns highlights a growing problem with malvertising and deceptive developer tools.
Given the rising adoption of macOS in healthcare administration and medical research environments, this attack highlights the urgent need to train staff not to trust unsolicited technical advice found through sponsored search results or unknown GitHub repositories. Establish clear protocols for system troubleshooting, restrict command-line execution privileges, and use DNS/web filtering to block known-malicious domains. Endpoint protection solutions should also be configured to detect unusual Bash scripts and monitor for unauthorized access to Keychain or sensitive files. In healthcare, where the compromise of even a single credential can jeopardize patient data, proactive awareness and policy enforcement are essential.







