Researchers at Trellix have uncovered a new Linux malware campaign that uses an unusual technique to deliver the open-source backdoor known as VShell. The attack starts with a phishing email disguised as a beauty product survey offering a small monetary reward. Attached is a RAR archive containing a file whose name includes a malicious, Base64-encoded shell command. When a script or terminal command attempts to process the filename, the payload is executed—without ever opening the file.
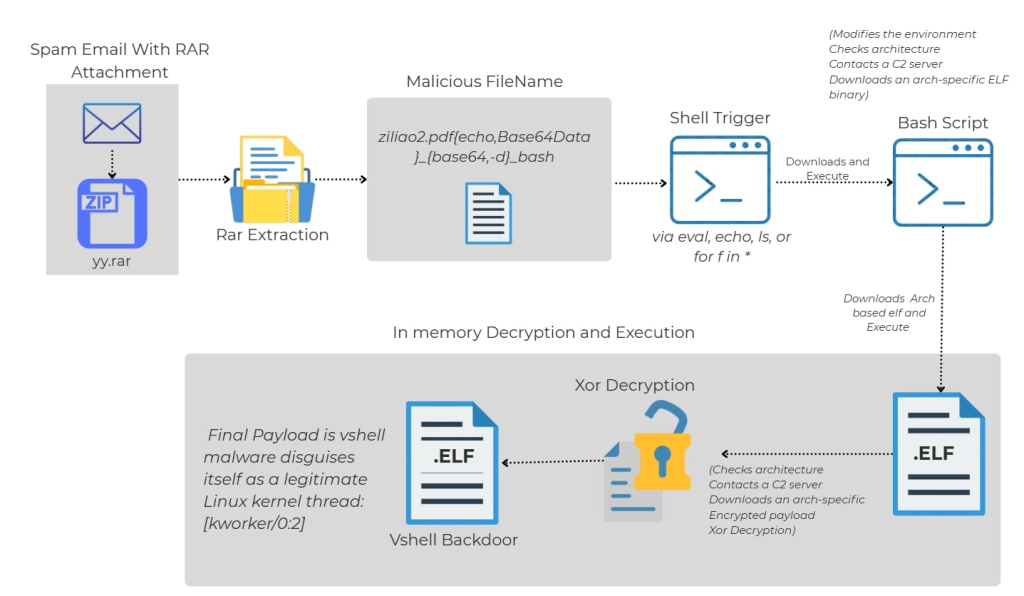
Source: trellix.com.
This attack exploits a common vulnerability in shell scripts where poorly sanitized filenames are passed to commands like eval or echo, enabling command injection. The stealthy technique bypasses traditional antivirus detection, as most scanners focus on file content and not metadata like names.
Once triggered, the malicious filename downloads and runs a system-specific ELF binary, which then communicates with a command-and-control server. It retrieves and activates VShell, a Go-based backdoor that supports remote shell access, file manipulation, port forwarding, and encrypted communications—all executed entirely in memory to avoid leaving forensic traces.
In parallel, Picus Security has identified another Linux threat called RingReaper, which abuses the Linux kernel’s io_uring framework to remain hidden. Instead of using standard system calls, RingReaper operates asynchronously to bypass detection tools, gather system information, escalate privileges, and clean up after itself. This highlights a growing trend in Linux malware that prioritizes stealth and evasive tactics over brute-force techniques.
Healthcare environments increasingly rely on Linux for servers, medical devices, and cloud infrastructure—making them attractive targets for advanced malware. Security teams should review shell handling practices, disable automatic processing of filenames, and deploy Linux-specific EDR solutions with memory-scanning capabilities. As attackers exploit even file metadata to gain control, it’s critical to adopt a zero-trust mindset and proactively harden Linux systems across the healthcare stack.