A new Android malware tracked as Android.Backdoor.916.origin is being used in targeted attacks against Russian business executives, according to mobile security firm Dr. Web. The spyware poses as an antivirus tool, branded with names like “GuardCB” and “SECURITY_FSB,” to trick victims into downloading and trusting it. Researchers found that the malicious app mimics the look of legitimate security software but provides no real protection—only fake scan results to dissuade removal.
Once installed, the malware requests extensive and dangerous permissions, including access to SMS, contacts, photos, audio, video, and even the ability to wipe device data. It can also activate the microphone and camera, capture keystrokes, exfiltrate messenger data from Telegram and WhatsApp, and stream the device’s screen. Dr. Web’s analysis shows the malware connects to multiple command-and-control servers, switching between up to 15 hosting providers to maintain persistence and evade takedowns.
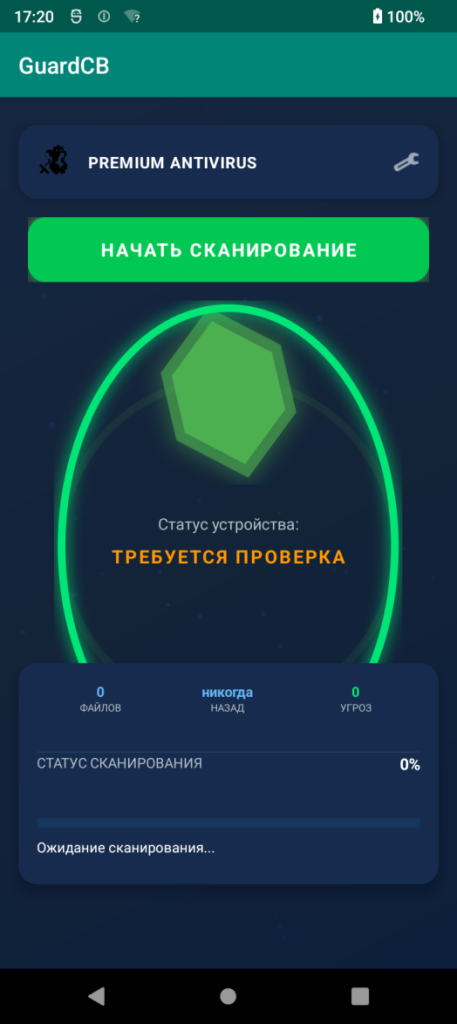
Source: drweb.ru.
The malicious campaign appears tailored specifically for Russian users. The app’s interface is only available in Russian, and its branding attempts to impersonate national institutions like the Federal Security Service (FSB) and the Central Bank. Researchers believe the operation began in January 2025, with multiple new versions released since then—evidence of ongoing development and refinement. Indicators of compromise (IoCs) have been published on GitHub to help defenders detect infections.
Dr. Web notes that this spyware represents a significant espionage risk, given its extensive surveillance capabilities and ability to impersonate trusted institutions. By leveraging the guise of authority, the attackers increase their success in tricking executives and business leaders into installing the malware on their personal or corporate devices.
While this campaign is currently focused on Russian business targets, it highlights a broader risk: malware masquerading as trusted security or healthcare applications. Medical organizations, especially those handling sensitive patient data, should enforce strict mobile device management (MDM) policies, restrict app installations to verified sources, and educate staff on recognizing fake security prompts. Given that healthcare leaders are increasingly targeted by advanced spyware, ensuring mobile threat defense is as robust as endpoint and network protection is essential to safeguarding both patient and organizational data.