Zscaler’s ThreatLabz has uncovered a major Android malware campaign involving 77 malicious apps that collectively racked up more than 19 million downloads from the Google Play Store. The campaign, which began with a fresh wave of Anatsa (Tea Bot) banking trojan infections, also delivered adware, spyware, and sophisticated malware families like Joker and Harly. The majority of the infected apps belonged to the tools and personalization categories—often perceived as harmless by users.
Joker, Harly, and the rise of maskware
Roughly 25% of the apps analyzed carried the Joker malware, a longstanding threat known for exfiltrating contact lists, intercepting SMS messages, and enrolling users in premium services. Another group of apps used “maskware”—malicious apps that convincingly perform legitimate functions while quietly harvesting data or installing secondary malware. A variant called Harly was also discovered using deep code obfuscation to evade Google’s automated review processes.
Anatsa trojan expands and evades
The Anatsa banking trojan has significantly evolved, with its latest version targeting 831 banking and crypto apps—up from 650. It now uses deceptive apps like Document Reader – File Manager to delay execution and avoid detection.
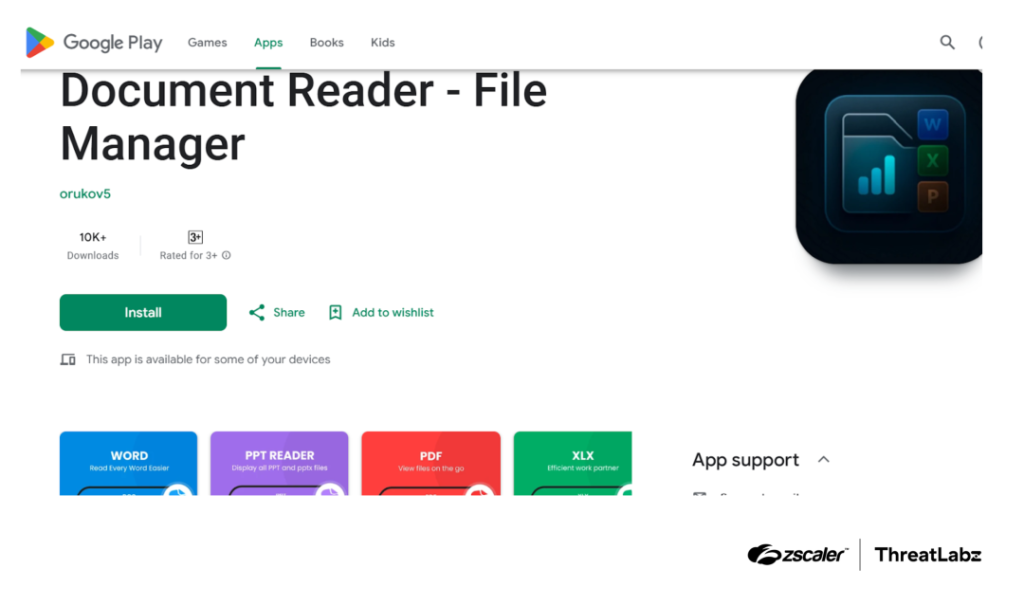
Anatsa decoy apps in Google Play. Source: zscaler.com.
Anatsa exploits Android Accessibility permissions to grant itself control, fetches phishing pages tailored to its targets, and includes a keylogger for capturing sensitive input. It also employs techniques like malformed APKs, DES string decryption, and emulation detection to bypass security tools.
Cleanup and lessons for Android users
Google has since removed all 77 malicious apps following Zscaler’s report, but the scale and stealth of the attack raise questions about the effectiveness of current Play Store defenses. Tools and personalization apps were the most common malware carriers, followed by photography, entertainment, and design apps. The campaign also saw a noticeable drop in previously active families like Facestealer and Coper, indicating a shift in attacker preferences.
Advice for healthcare and medical security professionals
This campaign underscores the growing risks of mobile malware—particularly for sectors like healthcare, where sensitive data and credentials are frequent targets. Healthcare organizations must assume that Play Store apps are not inherently safe. To defend against threats like Joker and Anatsa:
- Require mobile threat defense tools on all managed Android devices
- Enforce strict app installation policies and disable unknown sources
- Limit app permissions through MDM or endpoint protection software
- Monitor for signs of credential theft, particularly on devices with access to EHR, scheduling, or financial systems
As mobile devices become more integrated into clinical workflows, they must be treated as full-fledged endpoints with equivalent security oversight.







